The IPK® Solutions Approach
IPK® Underlying Premise: Use what’s HERE (Forward Error Correction or FEC), UNITED with Security Protocols...
Zero Overhead Encode (ZOE) – uses existing compute processing
- Supports ALL NIST Approved Ciphers, including your favorite AES encryption ciphers
- Post-Quantum Code-based Encryption approach (Classic McEliece)
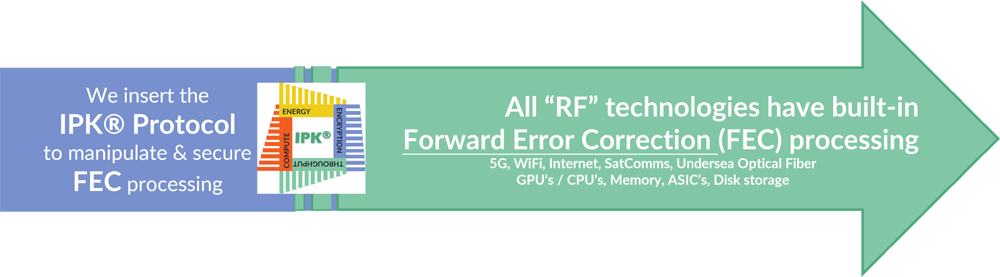
Significantly INCREASE Network Throughput while IMPROVING Link Security & Robustness!
Delivers MAJOR Energy Efficiencies from REDUCED Processing Overheads!
Simple & elegant – solves the four mega issues, and innovates what’s been “hiding in plain sight!”

IPK® is a patented software protocol that ties cryptographic variables to system variables including Modulation, Device Authorization and Authentication.
- IPK® “essentially scrambles and encrypts channel coding in part by randomizing the graph base of the LDPC channel coder/decoder”
Wait, there’s more… IPK® further cyber protects your data by allowing the user to multiply the complexity... add in one or all of IPK®’s “wheel of ciphering options” to each block or packet in your message.
A simple improvement is to deploy IPK® Secure Speed across your network and allow the user or application owner to apply their own preferred encryption approach.
The benefits of this deployment approach are:
- The network operates with the highest throughput and performance.
- All data is 100% IPK-ZOE secured (IPK®-zero overhead encode).
- The user or application is further secured to their preferred level of compliance.
- The encryption compounding effect is avoided.
- no more multiple, heavy compute ciphers at different layers in the stack.
- Network latency is eradicated.
- Compute economies and energy efficiencies are achieved.
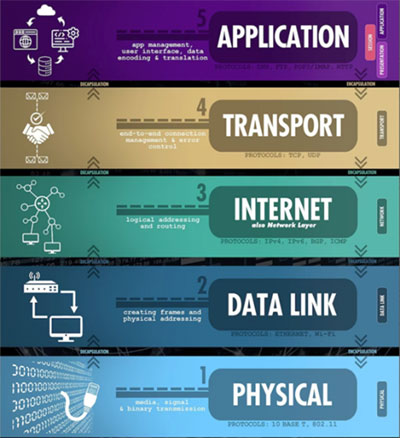
OSI Stack
- Layer 5 - Any Application or Website Layer
- PERFORMANCE
- Layer 3 / 4 - Cybersecurity in Network/Transport Layer
- EXISTING MADE BETTER
- AES256 encryption is 681 nS per block (14 cycles, often repeated) versus IPK is 13 nS per block (1 cycle)
- Layer 1 / 2 - Cybersecurity in PHY (Physical Layer)
- GAME CHANGER

Extending the IPK® paradigm further along the line into the Storage domain delivers impressive results. Incorporating IPK® Secure StorFast in your storage environment re-sets the benchmark for data I/O and retrieval. In an environment where milli-seconds micro-seconds and nano-seconds are the be all, applying IPK® within the Forward Error Correction (FEC) processing for Storage creates an acceleration in I/O and a profound improvement in data storage volume economies with almost a doubling of the storage capacity of your existing storage assets!
To learn more on how we can deliver profound outcomes in data storage, contact us for a conversation.

Available with our software development kit and supported by the IPK® Technologies’ Engineering Team, establishing a Proof of Concept (POC) is relatively quick and delivers a clear result:
- How much improvement could you see in your environment?
Working with our Test & Measurement Partner, and Coming Soon to IPK® Prospects will be the capability to emulate your environment in detail and demonstrate the “Art of the Possible”. Check-in with us on how you can get insight into where performance enhancements might be available in your environment.
Software: 40KB, No New Hardware Required
Optimizes Performance: Up to 300% network throughput increase
Supports NIST Ciphers a-la FIPS 140-02 and aligns with NIST Post Quantum Code-based Encryption submission
Reduces Energy Consumption: Reduced processing = energy savings
Fits In All Networks: Physical Layer to Application/Presentation Layers
Increases Security: Dynamic-change key lengths and/or key content
Improves Storage: 3x faster storage disk write throughput
Large Market Applicability: 5G, Satcom, Cloud Computing, IoT
